Shared Responsibility Model for Cloud Security

Cloud security
Security is one of the top priorities for every organization. Back in the day when companies deployed on-premises software, they were more or less sure that their data was secured as it was fully governed by their own efforts. Nowadays, when migrating to cloud computing, many organizations have concerns about security threats and data breaches, as they are not in the whole and total control of the infrastructure anymore.
In these terms, such cloud providers as Amazon Web Services and Microsoft Azure did their best to convince their users that there is nothing to worry about – provided security is sufficient enough and, in some sense, even more reliable.
Nevertheless, to state that and stay brutally honest with their customers, it was crucial to demarcate security-related responsibilities and articulate who is in charge of what. That is how the Shared Responsibility Model appeared.
What is the Shared Responsibility Model?
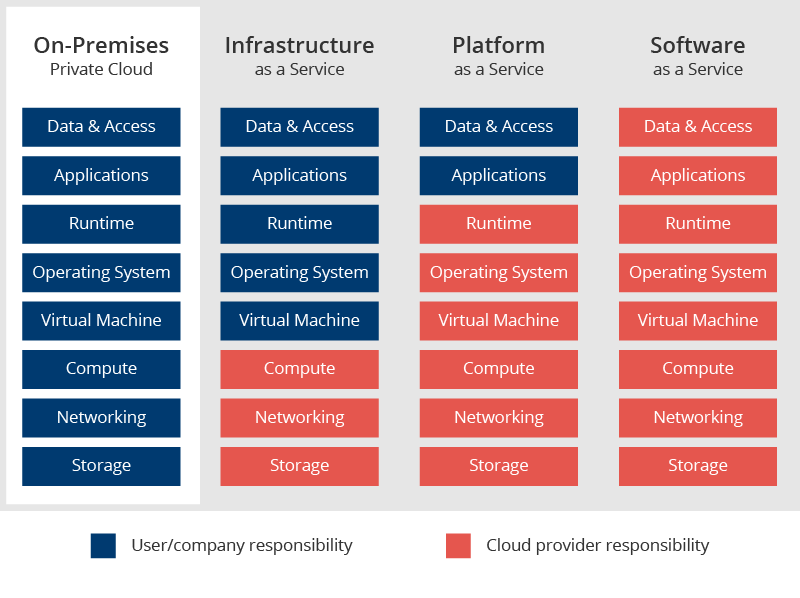
To start with, security responsibilities are divided between the organization and the cloud service provider. So a reasonable question arises: “Who is responsible for what according to the shared responsibility model?”
The answer is:
The cloud provider is responsible for the security of the cloud, while the company is responsible for security in the cloud.

So, a cloud provider takes the responsibility of making sure the infrastructure within its platform is built securely and reliably. They protect their servers from intrusion through a variety of protocols, they also offer backup, restore, and disaster recovery solutions. On the other side, the company, as the end-user, is responsible for managing the application, credentials safety, and encryption.
Enterprises and cloud providers – Working as a team
To create a secure cloud environment, the obligations should be taken seriously by both sides: if one of the parties neglects its part of the deal, there definitely will be consequences.
First of all, it’s important to understand exactly where the boundary between the responsibility of the cloud provider and the company is. It would be easier if there were a standard list of the obligations that every cloud provider has to take. Since there is no such set of rules, some misunderstandings may occur.
To not let that happen, companies should thoroughly examine what the cloud providers are taking care of and what stands outside of their liability area. For example, AWS takes the responsibility of protecting software, hardware, and networks, while Azure is mostly responsible for data centers, physical hosts, and networking.
End-users or companies are in charge of cloud platform configuration, information and data security, and IAM (identity and access management).
Additionally, the level of obligation can vary according to what the organization uses: on-premises software, IaaS, PaaS, or SaaS.
As Gartner claims, the vast majority of cloud security threats occur due to the end-users negligence, for example, sharing access with someone through an untrustworthy channel of communication or forgetting to log out of their account when using somebody’s computer. Users are responsible for keeping data secure and ensuring that the cloud providers they engage with meet all security and compliance requirements.
Why cloud security is important
Providing security of the cloud and security in the cloud is vital as even the smallest, at the first sight, omission can lead to serious problems. For instance, sensitive data loss can entail huge financial penalties from authorized organizations, or hurting business goodwill will definitely undermine trust in a company forever.
That is why it’s highly recommended to scrutinize what exactly you need to protect, what are the possible threats and how to ensure the required level of security.
In the abstract below we have collected some of the most frequent security threats and matched them with the best practices addressed to resolve problems associated with them.
Main security concerns and how to solve them
,
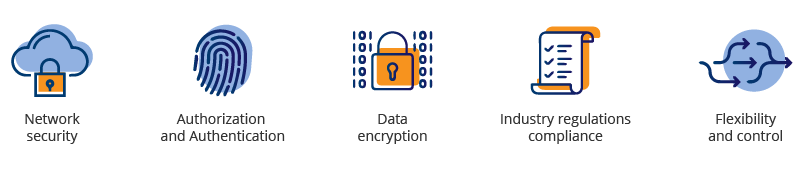
1. Network security
Concern: The rising number of endpoints, as well as their diversification, make the providing security task a lot more complex than it was before. We can also add here the fact that a lot of employees use their own devices and, in the era of the pandemic, – work remotely. Not a surprise that it makes the protection perimeter rather insufficient and as a consequence creates vulnerabilities.
Besides, hackers are getting more and more skilled and creative in finding new ways to gain access and getting sensitive information which can ruin years of hard work.
Solution: There are many things to consider in pursuit of providing network security but below we have listed main security tools and techniques to focus on right now:
2. Authorization and Authentication
Let’s, first of all, clarify the difference between authorization and authentication.
Concern: Access to cloud computing is carried out remotely, through the public Internet. While it simplifies the accessibility for team members or customers, it also increases the risk of unauthorized access to the company’s cloud resources. Security misconfigurations or credentials leakage may lead to this type of security issue.
Solution: Consider using services that offer identity recognition and access management features. It would also be beneficial to establish basic security policies for workers as:
The usage of several authentication practices is great, however, using the weak ones leads to trouble with cloud security. It’s crucial to authenticate through secure channels only in order to not fall into the trap of interception. The usage of channels like email or phone is strongly discouraged.
3. Data encryption
Concern: When the data is transferred to the client or server, such sensitive information like social security numbers, personal credit card numbers, and residential addresses can be leaked over the Internet and, in the worst-case scenario, intercepted during transit. It’s unwise and irresponsible to store sensitive data without any enhanced protective measures taken.
Solution: Implement encryption. For providing reliable encryption a company should create unique keys for every service and implement access restrictions according to the principle of least privilege. Permissions of the keys should be limited. One more point – keys should be updated regularly to be sure that even privileged users can’t compromise them and get full access to the company’s sensitive data.
Another point to be mentioned – businesses should control encryption keys. A company can give cloud providers access to the keys, but it doesn’t mean, in any case, that the responsibility for data safety lies on the vendors – the company itself is still the one who is in charge of safety maintenance.
4. Industry regulations compliance
Concern: Nowadays data is the most valuable asset a company possesses. Losing it or providing anyone with unwanted access to that data puts the whole company in danger of losing credibility, goodwill, and money. Particular laws and regulations make companies take their data privacy seriously as it affects personal privacy and security.
When talking about regulations – they depend on the industry. For example, the US government agencies have to comply with FISMA, while HIPAA is the regulation required for healthcare organizations. In case when a company violates outlined policies related to it corresponding fines and penalties will be imposed.
Solution: Compliance and security should go hand in hand. It’s more convenient and safer to work with a cloud provider who follows industry best practices to ensure security within the cloud infrastructure. Furthermore, the presence of a recognized certification is one more benefit for the organization.
To ensure your compliance efforts are both cost-effective and efficient, the cloud service provider should offer you the ability to inherit their security controls into your compliance and certification programs.
5. Flexibility and control
Concern: Many companies prefer multi-cloud architecture, so providing cloud security becomes even more complicated – it’s easy to overlook some misconfigurations or data leakage. The most disappointing factor is that the security threat can remain unnoticed by the IT department for a long time which is a total disaster for any organization.
Solution: Deployment of a cloud management platform is a good way to get total visibility of all used IT assets within the cloud, optimize the cost for cloud services’ resources, and monitor compliance policies.
Binadox is a good example of a tool that keeps businesses aware of the current compliance policy state apart from providing businesses with features for monitoring and managing numerous cloud resources. You can register for a FREE 14-day trial and experience its benefits.
Summing up
Creating a security strategy is an essential aspect when migrating to the cloud and its importance is not diminishing throughout the time of cloud services exploitation. In general, security provision is based on 3 pillars: protect, detect and respond.
Choosing the right provider will reduce the majority of risks related to the basic security of the cloud. Once a company learns how to successfully execute the developed security strategy which includes the best practices, policies, and tools, its business processes will improve significantly.